Three ways you might be letting them in, and what to do.

Can they? Sure.
Do they? Maybe. It’s easy to do, but hard to manage. It really depends on how you connect to your home machine and how aggressive your company is about tracking you.
Become a Patron of Ask Leo! and go ad-free!

Is your boss watching?
- If you connect to your work computer from home, the company can monitor your internet activity.
- If you install work software on your home computer, the company could include spyware.
- If you connect to your home computer from work, all of your communications with the machine at home could be intercepted.
- If this is of concern to you, the solution is to keep work and personal technology completely separate.
Any connection between your workplace and your home computer can open the door for corporate monitoring.
Most common right now are work-from-home scenarios, where you connect to work from a home computer. I’ll save your question — connecting to home from the workplace — for last.
1: Connecting to the workplace from home
When you connect your home computer to your workplace, you typically route all of your internet activity through that work connection.
For example, let’s say you make an innocent, unrelated-to-work Google search. Normally, that means your computer reaches out to Google to submit your search and get the results.
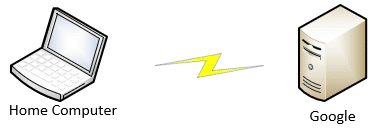
If, however, you happen to be connected to your workplace, then instead of going directly to Google, your web search is routed through your workplace’s network.
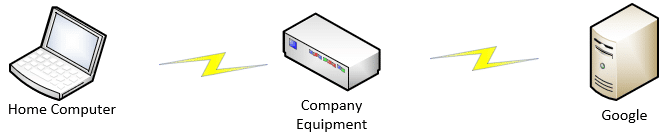
When you connect to your workplace, your company often uses a VPN to protect that communication. The VPN doesn’t know what traffic should be local or not, so it’s all routed through your company. This is almost exactly as if you were at work, where all the traffic would be routed through your company’s equipment by virtue of your being there.
And of course, any traffic that travels through your company’s equipment can be monitored by your company. Thus, your employer can spy on your home computer’s activities.
2: Installing work software at home
It’s not uncommon to install software from work on your home computer in order to do your job. Particularly if your workplace uses custom or company-specific tools, you may not be able to get them anywhere else.
The net result is that the software you install on your home computer could have an unexpected payload: spyware.
Regardless of whether you connect to your company’s network or not, spyware installed on your system can do anything. Your workplace could spy on your home computer’s activities whether you’re actually working or not. Understanding how much (or when) you’re working may be the reason they want to monitor you.
3: Connecting to home from the workplace
Regardless of how you connect to your home computer from work, it’ll be through the company’s networking equipment. That means they can monitor all the data being exchanged.
Even if the connection you’re using is theoretically encrypted end-to-end, there are techniques that could be put in place to allow the company to monitor the contents of those encrypted conversations (see below).
They don’t even have to get that esoteric. Once again, they could install the equivalent of spyware on your work machine to record your keystrokes, screenshots, and more. It is their computer, after all, and they can install on it what they will.
Protecting your privacy
If corporate snooping is of concern to you, you really have only one option: keep your personal and work technologies completely separate.
Not only does that mean not using work computers for things personal and vice versa; it also means never connecting work equipment directly to your home network — use a guest network, at a minimum.
Well, you have one other option, of course: finding a different, more trustworthy place to work.
How likely is all this, really?
I know that much of this smacks of paranoia. For most people, I return to my “you’re just not that interesting” admonition. In general, what you and I do outside of work is of little interest to our employers.
But…
Particularly in an age where working from home is more and more common and employers have a more difficult time keeping tabs on employees, there may be some who will be concerned enough to consider spying. Even when we’re back in the workplace, when liability is involved, they may feel a duty to monitor what you do, including your non-work activity, if it happens on their equipment.
So yes, absolutely, your workplace can spy on your home computer activities if you inadvertently allow them to.
Whether they actually do, I’m afraid, only they can answer.
Spying on encrypted connections
Most remote access tools and VPNs are encrypted and secure by design.
Or are they?
One technique that surprises many people is the corporate ability to spy on otherwise encrypted connections. It’s not clear how common this is, but it’s technically feasible to do without “breaking” encryption at all.
Techniques I’ve heard discussed work like this:
- First, remember you don’t really control your work computer. Hidden proxies, alternate encryption certificates, and more could be installed by your company.
- When you attempt to connect to a remote computer, it’s transparently intercepted by a corporate proxy sitting between your work machine and the internet.
- Your connection to the proxy is encrypted, but the proxy is able to decrypt, examine, and possibly log the data. It then re-encrypts the data on the connection to the remote destination. The same applies to the reverse path.
- You’d never know this without examining the characteristics of your connection very closely and knowing what to look for (except perhaps for a little slowness).
This approach is technically complex, so I wouldn’t expect a company to set it up unless they had reason to or were particularly paranoid.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!




Quote: “Can they track what I do on my ***home*** computer”
Isn’t the question about whether the HOME computer can be watched rather than the work computer?
Answer:
It is unlikely that your computer could be tracked from your workplace if you connect via Remote Desktop. However, there are some ways that your workplace could track it…
1) In the remote desktop client there is a way to let your own drives appear on the remote computer as network drives (under the advanced tab). If you do this, someone near the computer could possibly look through your drive.
2) When you connect, it is possible for your IP address to be tracked back to you (e.g. via packet sniffing as mentioned above). Although this would not allow anyone to read the packets (due to encryption), it could allow them to exploit a vulnerability on your computer. This shouldn’t be a problem as long as you have a decent firewall…
There may be other possibilities but I now have to go…
—
“Isn’t the question about whether the HOME computer can be watched rather than the work computer?”
Yes, of course. But to access the home computer you’re doing it THROUGH a work computer. The article describes how by monitoring what happens on the work computer you can monitor what you’re doing on your home computer.
What it really boils down to is does your company have a policy in place that restricts this kind of “idle” screwing around, and what the penalties are and did you sign the piece of paper agreeing not to utilize company assets for personal gain etc. If you cannot justify acessing your home computer and the above is true, it doesn’t matter whether they can track you, they just have to prove you used work equipment for “joysurfing” (for lack of a better term) and that makes you liable for the consequences of the action. They don’t have to know what you did specifically, they just have to be able to show you were somewhere, doing something that you agreed not to.
I’m connected via RDP from work as I type this :)
And with the crazy fast internet upload speeds now avaible it’s quite nice actually.
There is no apparent way to extract what you type or see in an RDP session unless they are running a keyboard sniffer or capturing your screens a session to your desktop.
Yes that RDP traffic goes through the employer firewall, but it it’s a giant blob of nothing. Can they see traffic volume from your work desktop to an IP that could be linked to you .. sure. But the volume would the look the same if you had a something updating on the remote monitor.
You are probably safe as long as you get those TPS reports done on time.
As I hopefully clarified in the updated article, even encrypted connections are subject to inspection as they cross the corporate network. It takes some doing by a knowledgeable IT staff, but it’s possible. Put another way, I would not depend on it being impossible.
“If you install work software on your home computer, the company could include spyware.” If they were caught, they would be liable for a big law suit, so I would imagine that on is quite rare.
In my case, the educational software I use at work is third party, NEO LMS and Zoom. I doubt if NEO LMS would turn over any information to my university other than what I do on their website. They can see everything I do on it and there’s even a warning that any emails sent over their system can be monitored by the school. As for Zoom, the account is mine and the school just reimburses me for the cost of using it.
My question is, Can a company whose work you do on their website see anything else you do on the internet anyway other than a drive-by download?
You’re assuming we all live in the same country with the same laws, AND you’re assuming we all agree on what “spyware” means. Corporate spyware could be much more subtle and limited than the malicious stuff we think about when we hear the term. It might even be limited enough to not qualify as spyware in a legal sense. ALSO, on top of all this, is your employment contract or whatever paperwork you signed when you joined — you may have given them explicit permission to do all of this and more without realizing it.
My method for accessing my home PC from work has been via TeamViewer or Splashtop. Assuming I’m not transferring files back and forth, the only thing that could be harvested by my company are keystrokes, correct? As far as I know, these remote control apps do all the work on the remote end and just update the screen/view on the local side.
Keystrokes, display images, sound, printing, file transfers — anything that flows between the two machines could theoretically be captured.
I once installed a keylogger on my computer to check out which sites my girlfriend’s kids were visiting (it eas her request). It recorded every keystroke, revealing the password to every login, it took a screenshot at intervals determined by the user. In other words, absolutely everything done on the computer.
Leo, you wrote:
“Your connection to the proxy is encrypted, but the proxy is able to decrypt, examine, and possibly log the data. It then re-encrypts the data on the connection to the remote destination.”
There is a formal name for this scenario: it’s called a “Man-In-The-Middle Attack.” And it’s a pretty classic one, too.
You might refer us to some computer privacy site(s) where we can all learn the joys of Alice, Bob, and Eve. :/
While it technically is a man-in-the-middle, I’m reluctant to come out and call it an “attack”. Quite often it’s simply a side effect, or configuration choice, made by the company you work for. Regardless of what it’s called it’s important to realize that not everything might be as secure as you think.
Hi, I use a different [mac] machine, via VPN, to connect to work, but via my home network. In your article, you said, ” it also means never connecting work equipment directly to your home network — use a guest network, at a minimum.”
How do I ‘use a guest network,’ while having both my personal pc + my work’s mac machines connected via my home wifi?
A guest network is a feature of the router. If it has that feature, use it. (It’ll almost certainly be called that.) If not, a VPN, as it sounds like you’re using it, is the next best thing.
(It’ll almost certainly be called that.) If not, a VPN, as it sounds like you’re using it, is the next best thing.
I want to resurrect what Matt Taylor said in 2007 (see old comments): “What it really boils down to is does your company have a policy in place that restricts this kind of “idle” screwing around …”. What the heck is this guy doing connecting to his home computer from work? In most serious work environments this would be a security violation. In any government or government contracting environment this would be a reason to fire the guy and report him to the FBI.
Actually, the question is not so much what is he (or she) doing connecting to home from work but vice versa. And that is the scenario that has come to the fore with Covid 19.
For people who are now working from home and connecting to their work system(s) they need to be able to access it. But the company needs to ensure that nothing inappropriate is happening i.e. viewing porn, accessing Tinder etc., because they could be dangerous to the work network, plus, your supposed to be working.
Read the original question: “If I connect to my home computer from work, can they track …”.
If people have an account with a School District for “Employment Purposes/Application,” and you “Pin” a District Tab on your personal computer, (comp. not owned by School), can they randomly spy on your Internet Activity? What would people have to watch out for? Can PC-Matic block these intrusions or give you notification of such a process in action?
Technically possible… realistically not likely. Used to work for a Government Department and we were informed that when connecting to the network, back then (2010-20120 we had some clunky app to install to do that, anything we did was accessible, and stored, on the work system. A requirement btw for Public Records Act (in New Zealand).
Solution? Have a cheapo computer to use for connecting to work, and don’t use your personal computer at home to do work’s work. We used to be able to buy 3 year old work computers as they were “technically” past their useful life. As I recall we paid about $100 for them. And while they weren’t the fastest machines around, obviously, they did the job and kept our “personal” PC’s safe from any malicious prying at work. But as the IT head honcho said, unless malware or porn showed up in the records then we’d be safe. But rules could easily change due to Govt mandated rules or, as he succinctly put it, a new psycho manager. LOL And yes we ended up in the IT team getting a manager who was a bit of a control freak. Fortunately he was “suggested” to look for work elsewhere. He took the hint and did so.
Keeping a tab open — or just visiting a web page — shouldn’t allow them to track anything.
Here is how I connect to my work environment from home on my personal pc… I sign into a specific web site with my user credentials and a VPN access portal is set up . From that web site, I log in again with my work credentials (just like if was in the office) and all business apps are accessed on THEIR remote servers. (actually, this is basically the same protocol when I am in the office, everything runs through web browser connection.) All of the MS Office apps, as well as business specific apps (e.g. SAP database) are on their server. None of these reside on my personal computer. I don’t use MY MS Outlook to access company email. They run Office 2013, (I run Office 365) which runs off of their server on my system. If I access the internet (via Chrome or IE) from within that browser link, I am accessing through THEIR server as well. However, if I work outside of that browser window, I am accessing MY apps on my pc that are in no way connected to their server. At least that is what I am led to believe. Can they ‘jump’ the VPN through that web browser and still access my personal data?
There seem to be many questions such as this. The basic answer is “yes, they can do anything”. Leo’s article addresses this. The reason that they can do anything is that the technology exists and the know-how exists, so if they want to “jump the VPN” or use the browser to access your data, they can. In the Big Blue Box Leo said: “If this is of concern to you, the solution is to keep work and personal technology completely separate”. That means use different entirely different computers. But, even that provides no guarantee of preventing snooping because you’re likely using the same router and internet connection.
You mix together “home computer” and “work computer” in your discussion. If the computer is provided by your work, they can put anything on it. In 2020, I can say for sure that my employers installed programs that monitor which apps run, network connections, downloads, and cannot be stopped or uninstalled. These programs would run all the time whether you were working or not.
But if your employer lets you use a computer YOU bought to connect to work, it’s different.
1. if you connect to work by just opening web pages, it would be difficult for them to monitor what you do in other apps or even other browser windows (basically equivalent to putting spyware on your computer by opening a web page).
2. if you installed apps from your company on your computer, they could certainly contain spyware. I question if it would be legal for it to run when you are not working, but don’t know.
it’s not clear to me that it would be legal
1. Your employer might not be able to monitor what you do on your computer, but they can see everything you do over their network, so unless you use a VPN or stick with httpS: websites. But they still could see you are using a VPN and without a VPN, they could see which websites you were visiting. And using your browser in stealth mode doesn’t offer even a tiny amount of protection as all stealth mode does is clear your browser cache, cookies and history from your computer.
2. I’m not a lawyer, so this isn’t legal advice but I’m sure installing spyware on your personal computer is illegal.
I work as an independent contractor and have numerous clients. (I work using my personal computer.) A new client recently wanted me to download their remote access software on my pc to complete the job. When I inquired what their software would access on my personal computer, and told them I couldn’t compromise my other clients work or the non-disclosure agreement that I signed, they wouldn’t answer, and told me to get a new computer to use if I was so worried.
Apologies for the stupid question, but does remote access software allow access to what’s only on the screen at the time or to the entire computer files etc?
Remote access software allows access to everything.