Sending an encrypted document as an attachment is a pretty reasonable approach to sending information securely in what is otherwise an unsecure medium – email. Even though there are approaches to encrypting email, they’re either obscure or complex, and not as ubiquitous as we’d like.
Encrypting individual files can also be an important step to your own secure data management.
I’ll look at two approaches to encrypting a single file which can be sent securely in email, yet typically, decrypted easily by just about anyone.
I’ll also take special care to call out the weakest link most likely to allow your encryption to be cracked. It may not be what you think.
Become a Patron of Ask Leo! and go ad-free!
AxCrypt
AxCrypt 2.01 is a free utility for Windows, designed to securely encrypt single files. It’s almost an ideal solution for the situation we’re addressing.
After installing AxCrypt and creating an AxCrypt account, a new context menu is added to Windows Explorer. Right-click on any file in Windows Explorer, and you’ll see this:
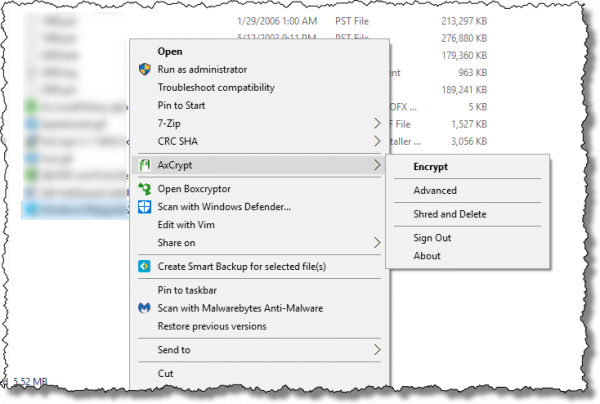
The most relevant action is Encrypt, which encrypts the selected document, removing the original and replacing it with the encrypted version as a “.axx” file.
While previous 1.x versions of AxCrypt would allow you to specify a simple passphrase as the encryption key, the current version uses an encryption key based on your AxCrypt log-in account. This makes encryption and decryption nearly transparent, as there’s no prompt – the action just happens as long as you’re logged in to that AxCrypt account.
Important: do not lose your AxCrypt account password. If you have to reset it, you will lose access to all files previously encrypted using your account. There is no recovery back door.
The free version of AxCrypt is a nearly perfect solution when you’re simply encrypting files for yourself. Logging into your AxCrypt account is enough to make encrypting and decrypting files easy across all your Windows machines. (Additional platforms besides Windows are promised, but not yet available at this writing.)
Sharing encrypted files
Back to our original question. AxCrypt 2.0 free works well when you’re the only one needing access to your files.
If you need to share your encrypted files, there are two quick approaches:
- AxCrypt 2.0 Premium (which is not free) allows you to give specific other AxCrypt users the ability to decrypt the files you encrypt.
- Use a different, albeit it slightly more cumbersome, tool.
Since AxCrypt is also currently Windows-only, it’s that second approach you’ll need if your recipients are not running Windows.
7-Zip and Zip files in general
The Zip format, formally referred to as an “archive”, is primarily intended to let you bundle multiple files together into a single file that is compressed to save space. You can password protect the result, which encrypts the contents.
There’s nothing at all that says you must include several files. As a result, .zip is also a fine format for encrypting single files.
I’ll use 7-Zip for my example, but the .zip file format is ubiquitous, and zipping tools are available on almost every platform, including Windows, Mac, and Linux. A file encrypted on one should be decryptable on any other.
Open 7-Zip and navigate to the folder containing the file you wish to encrypt. Right-click on the file, select 7-Zip, and then Add to archive.
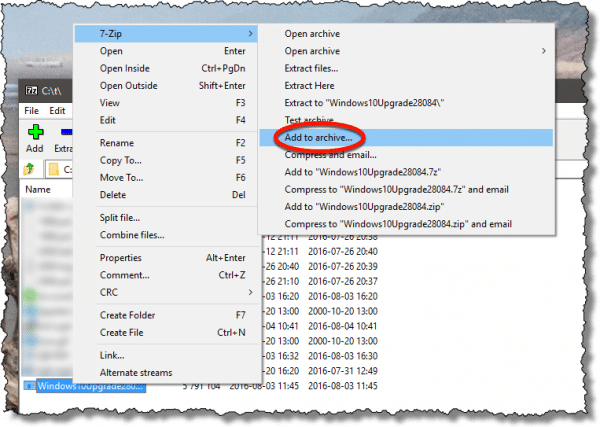
The other quick options, like “Compress to ‘<filename>.zip’ and email” look convenient, but they don’t encrypt – thus our use of the “Add to archive…” option.
In the resulting dialog, there are a few settings we want to pay attention to.
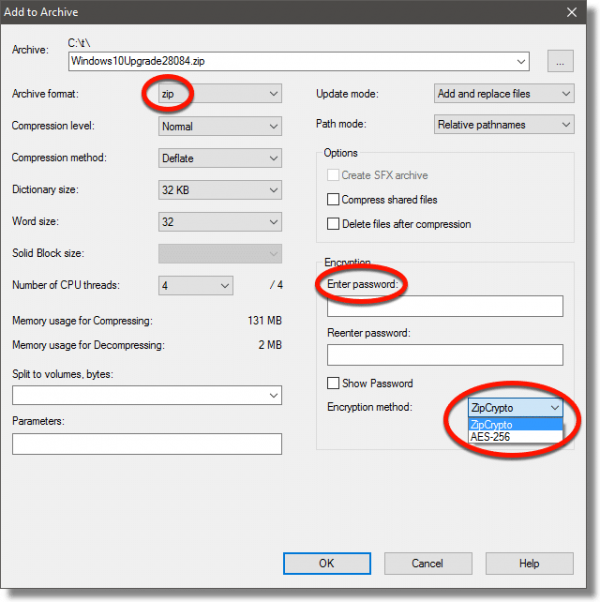
- Set the archive format to “zip”. This ensures that 7-zip, specifically, is not required to extract the file. Anyone with a Zip program (and the password) can open it.
- Enter a password – more ideally, a passphrase – to secure the file.
- Select the encryption method: ZipCrypto, the default, is the most compatible across different unzipping programs; AES-256 is somewhat more secure. I’d generally recommend AES-256, unless your recipient tells you that they are unable to decrypt it.
Click OK and 7-Zip will create your .zip file.
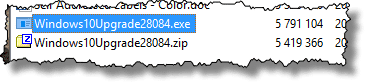
In this example, I encrypted the Windows 10 Anniversary Upgrade utility file, Windows10Upgrade28084.exe into Windows10Upgrade28084.zip. Note that unlike AxCrypt, Zip utilities leave the original alone. You may want to delete that if you don’t want an unencrypted copy of your file to remain.
You can now send that file to others, and they can use their zipping program to extract the contents of the file. (Be sure to share the passphrase separately – ideally via a method other than email in this case.)
Using 7-Zip in a command line operation
I’ll be honest and say that I’m not a big fan of the graphical interfaces of most zipping utilities. They’re too confusing and cumbersome to me.
Here’s what I really do to zip a file: in a Windows Command Prompt, I type:
7z a -tzip -p example.zip example.doc
Where:
- 7z: Is the 7-zip command line program.
- a: Means that we are adding a file to an archive.
- -tzip: Indicates that the type of the archive to create is a zip file.
- -p: Causes 7-zip to prompt for a password to be used to encrypt the file.
- example.zip: Is the zip file we are creating (or, if it exists, the zip file we are adding to).
- example.doc: Is the file we are adding to the zip file.
To decompress and decrypt the zip file back into its original file or files, the command would be:
7z x example.zip
Where the “x” command simply stands for extract.
One Zip drawback
One of the characteristics of the zip file format is that even if it’s encrypted, the list of filenames it contains remains visible in unencrypted form. The net effect is that in our example, someone without the password may not be able to see the contents our file, but they can still see its name.
The traditional solution to this is to rename the file to something obscure before zipping, or to zip twice. Zipping twice has the added benefit of preserving the original filename for the intended recipient.
- Zip the file once, without a password, into a single .zip file with an appropriately obscure name, like “zippedfiles.zip”.
- Now, zip that file again into another .zip file, this time specifying an encryption password.
The net effect of this approach is that both the contents of the files, as well as the names of the files contained within the original zip, are protected.
You are the weakest link
There’s often a lot of discussion around what encryption technology is the “best” and least susceptible to cracking. That’s an important discussion, and in my opinion, the scenarios above are sufficiently secure for all but the most demanding applications. (Depending on your needs, you can delve deeper into different algorithms used in most zipping programs, or dive into public key encryption with PGP/GPG.)
However, hackers rarely gain access to encrypted files by cracking the algorithm.
Instead, they simply hack the password.
Picking a weak password makes that kind of discovery easy.
Unlike hacking passwords online, in this case an attacker can spend as much time with your encrypted file as he or she would like to. In fact, they can throw as much computational power at it as they might want to simply perform a brute force attack – trying every possible password.
An eight-character password is nothing to an offline brute force attack these days.
That’s why most of these programs don’t use the word “password,” but instead default to “passphrase”.
Rather than using a short eight-character password, instead use a longer phrase consisting of four or five words that total at least 20 characters or more. No matter how you do the math, this is virtually uncrackable using current brute force techniques.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!
Podcast audio
More for Patrons of Ask Leo!
Silver-level patrons have access to this related video from The Ask Leo! Video Library.


with 7-zip-
make sure to use zipcrypto, i’ve found that sharing AES type encrypted files are hard to open on other systems that don’thave 7-zip on them (if you make a self-extracting file for example)
just my two cents
YES. A document encrypted with ZipCrypto can be easily opened with the unzipping utility that automatically comes with Windows. But if it’s encrypted using AES-256 (even if it’s in the Zip format), you can’t. You’ll get an error saying “Windows cannot complete the extraction. The destination file could not be created.” The only way you can open it is with 7-zip.
So if you want to share an encrypted document with someone who isn’t particularly tech-savvy and doesn’t have 7-zip on their computer, make sure you encrypt it using ZipCrypto, not AES-256.
How do you get the passphrase to the person you send the file to?
18-Dec-2012
Wow..great article…only 2 prob’s 1. Gonna have to read it multiple times more and 2. A question..Where are all these longer and longer passwords goin to lead to in the end ?????????????
18-Dec-2012
Richard, that is the weak link. Most people actually send the password in the email or another email.
Text or phone are what I use.
Here’s another approach for “sharing” a password.
Person A and Person B send each other 1/2 of the password. Using an agreed upon method of combining the two halves, we get a password that was never sent in one communication.
Example : Person A sends a string of numbers and Person B sends a string of numbers. The two numbers are added or multiplied and we have a “secret” password.
Example : Person A sends a series of “words” and so does Person B. The word strings are combined by alternating a word from A and a word from B, in the order they were sent. A “secret” password results.
Or, as already suggested, you could just call each other on the phone.
Leo, I think you need to ugrade your copy of 7-Zip. Mine has a checkbox option to excrypt the file names as well so there is no need to double zip anything. It should appear just below the encryption method option in your example.
18-Dec-2012
I tried copying and pasting the pass-phrase from LastPass when right clicking on the document. There was no shortcut menu. This seems to make encrypting a file with a long password impossible for those of us who don’t want to deal with a password outside of LastPass.
18-Dec-2012
My apologies. My comment about encryption didn’t mention that it was in reference to AxCrypt
@Frank. I do not understand why it does not work for you. The Rt click copy and Rt click paste work correctly from Lastpass to Axcrypt. I just copied my 21 character password from Lastpass and pasted it into the encrypted file of Axcrypt. The other method you can use is Ctrl +c to copy and Ctrl+v to paste the passwords or phrases. I’d give it another try Frank.
If I mount an encrypted folder/partition (that was previously encrypted with Truecrypt), that essentially opens up the folder so I and my programs can now use all of it’s contents. I would guess that I could then use AxCrypt to encrypt one file and email it to my not-so-computer-savvy friends. Then, when I dismount, it’s back in the fully encrypted form on my hard-drive and is fully functional in the email as you explained above. Am I right?
18-Dec-2012
But the article said about AxCrypt: The most relevant action is Encrypt, which encrypts the selected document, removing the original and replacing it with the encrypted version as a “.axx” file.
As I read it if the original is removed within the Truecrypt container and replaced with an encrypted version, when the Truecrypt container is dismounted that particular file will now be doubly encrypted. When you remount the Truecrypt container that one file will still be encrypted by AxCrypt and will have to be decrypted by AxCrypt before it can be used.
For reasons I have not been able to get a straight answer too, our ISP in Canada, Telus, does not allow emails, with encrypted .zip files attached, to be sent.
There is no problem sending non-encrypted .zip files or encrypted files using the 7-Zip .7z format.
This is the message we get back from Telus with encrypted .zip files.
“The message could not be sent because its size exceeded the server’s limit. You can use the option, located in Tools | Accounts | Properties | Advanced, to break messages into smaller parts. Subject ‘test ‘, Account: ‘a*******k@****.ca’, Server: ‘mail.telus.net’, Protocol: SMTP, Server Response: ‘552 Password protected zip file found inside of the email’, Port: 25, Secure(SSL): No, Server Error: 552, Error Number: 0x800CCC6D”
19-Dec-2012
Leo … AxCrypt is easy to use. Another great tip. Thank you. … Al
One problem I have had is that a lot of email providers will not allow you to send a file with an EXE or Zip extension. I assume that is for security reasons.
My work around in that case, is to change the extension to BBB or some other non-common extension. Send the file and let the recipient know to rename with the EXE or ZIP extension.
Of course, this assumes a Windows operating system.
Re: Telus blocking encrypted .zip files.
Our last tests were with 535 and 2048 byte files. Can’t get a whole lot smaller than that.
We even tried renaming the .zip to something else and they still got blocked.
Unencrypted, the same .zip files are sent fine.
Re: Telus
I doubt it’s a bug. It’s probably a deliberate choice by Telus in the interest of security. The “file size” message is likely a semi-generic error. Note that the error message also includes the phase “Password protected zip file found inside of the email”.
Telus, like other ISP’s, probably wants to be able to scan attachments for viruses. Scanning, of course, is exactly what users are trying to prevent by encryption! In this case, why not use a free file sharing site like Mediafire to share the (possibly encrypted) files?
One additional thing for those who need to eliminate the original unencrypted file from their computers, you would need to install a file shredder utility to fully erase any traces of the original file from your machine. This wouldn’t be necessary for most people, but I’m including that suggestion for those who need it. Sdelete is a command line program, but I find it easy to use. You can also google to find a wiper with a graphical user interface.
http://ask-leo.com/secure_delete_what_is_it_and_do_i_need_it.html
http://go.ask-leo.com/sdelete
AxCrypt used to come bundled with a PUA/PUP (OpenCandy), which is somewhat ironic given that it’s a security app.
https://www.axantum.com/AxCrypt/Freeware.html
I have no idea what, if anything, it’s bundled with now – OpenCandy was shut down last year – but it’s certainly not an app I’d recommend.
I downloaded and installed AxCrypt fairly recently, and there were no offers for any kind of unwanted programs. In any case, if you are careful, you can avoid any unwanted software which comes bundled by choosing custom install and reading the screens to find out what they are trying to install. Free software is a bit of minefield, but the mines are easy to avoid if you are careful.
It all comes down to the risk one is willing to take. I’ve downloaded my share of software bundled with pups and I haven’t been burned by an unwanted program in many years. If a good and useful piece of software is only available from a source which bundles it with pups, I carefully read all of the screens and only agree to install the software which the agreement says is installing the software I want. In fact, I treat all freeware like that and I assume that everything I download might have a pup or three. In addition, pups which come bundled with software from reputable companies (OK sounds like an oxymoron, but I’m talking about companies which aren’t breaking the law) are relatively easy to remove by following the instructions of this article. How Do I Remove PUPs, Foistware, Drive-bys, Toolbars and Things I never Wanted
Especially Malwarebytes and Adwcleaner
I’ve helped many people afflicted by foistware, and the software recommended in that article worked every time.
“It all comes down to the risk one is willing to take.” – Zero. Why take any risk when there no-risk alternatives available.
“I’ve helped many people afflicted by foistware” – Which, perhaps, proves that it’s not so easy to dodge and that people would be better simply avoiding programs that come bundled with crap.
I didn’t write that reply to your comment so much for your sake as you have already made an informed decision. I mainly wrote that comment for others so they could understand the risks and make their own decision. One of the most dangerous activities in the world is riding in a car, yet most people are aware of the risks and take the necessary precautions.
“One of the characteristics of the zip file format is that even if it’s encrypted, the list of filenames it contains remains visible in unencrypted form.” – 7_Zip supports the encryption of files names when the 7z is format is used.
Leo addressed that in a previous comment:
But you can zip it as a .7z file and check the SFX box which would save the encrypted result as a self extracting executable (.exe) which anybody with the password should be able to open, with no need for any unzipping utility.
That’s a mighty fine idea, I must say!
It would be a perfect solution but for the sad fact that no ISP, email website, or email program (or at least, Windows Live Mail) will allow .exe file attachments anymore. :-(
Good point. There is a workaround for that. Rename the the extension of the .exe file to something else, like .xyz and it will be sent. Then let the recipient know they should rename the file back to .exe.
So rename them or zip them.
Zipping .exe’s doesn’t work with GMail and possibly others. I used to .rar them, but some people couldn’t handle .rar, so I switched to changing the extension (last 3 letters) and telling the recipient to rename them to .exe.
If they’re on a PC.
Right, but that’s only the compatible with 7-zip. I’m looking for generic compatibility here so you can safely email a file to a friend without worrying about the tool used. Zip is built in to all major platforms these days.
If you want to send an encrypted message without any hassle, there is a very simple method that most people are using all of the time without even realizing they are using it. Whatsapp, Skype and Facebook Messenger (coming soon) use end to end encryption. That means the data leaves your computer or device encrypted and isn’t decrypted till reaches the other person’s computer or device. Neither Facebook nor Microsoft can decrypt those files. Other messaging programs might do the same, but those are the 3 most popular, and I don’t know anybody who doesn’t use at least one of those. Of course, the message is unencrypted on your device, but you’d have to decrypt them anyway and have them reside, at least for a time, on you device.
Or you could use an encrypted file-sharing service such as Dropbox.
It’s unencrypted on Dropbox’ servers.
Use a shared folder and the encryption will be end-to-end.
Data is encrypted on Dropbox servers (I wasn’t totally correct about that in my previous post), but Dropbox itself can decrypt those and would have to turn the data over if requested by a judge. That isn’t true end to end encryption where the 2 communicating computers exchange keys. I don’t see how a shared folder would allow for a key exchange.
Ummm…. no. Or, rather, not encrypted enough. The file transfer will be encrypted, which is nifty, but ….
Basically if Dropbox could decrypt the file (say, in response to a court order) then I don’t consider it encrypted “enough”.
Generally file sharing services that have a web interface, as Dropbox does, have the ability to decrypt your files. Hence using things like BoxCryptor to add a layer of your own encryption that they can’t penetrate.
“Basically if Dropbox could decrypt the file (say, in response to a court order) then I don’t consider it encrypted “enough”.” – True, but it doesn’t really concern me. Or, at least, it doesn’t concern me any more than the possibility of a bank employee peeking at my financial details or a doctor’s employee peeking at my medical records. If I were to be using Dropbox to store sensitive information relating to, say, intellectual property worth millions, I’d obviously feel differently.
Storing files on Dropbox which Dropbox can decrypt is fine for you and probably a lot of people, but that’s not good enough to recommend to users without being explicit as to the shortcomings.
Leo wrote: “the current version uses an encryption key based on your AxCrypt log-in account” and “The free version of AxCrypt is a nearly perfect solution when you’re simply encrypting files for yourself.”
Doesn’t this mean that you lose the ability to decrypt your files if the service goes out of business? If so, that seems to be a major weakness considering how ephemeral tech companies are in the world. Admittedly this is true for any cloud-based service, but people need to be aware of this risk and not put all their files in one encrypted (cloud-based) basket. Always make sure you have local backups of those critical files (and possibly use a local program like 7-zip to encrypt those).
Or worse, does this mean that you must have on line access to your AxCrypt account to decrypt a file? What if you’re off line? Is your AxCrypt “account” local to your machine or on AxCrypt’s server?
Lots of questions and a general problem with more complex schemes in that you may be secure but you can’t be sure because you don’t know EXACTLY what is happening to your data.
As I said above, AxCrypt used to come bundled with OpenCandy, which most security programs would block. Whether or not it’s still bundled with extras, I cannot say – but it’s certainly not a product/company that’d I’d recommend.
Microsoft should have long ago provided a built-in file encryption feature where Windows users could exchange encrypted files between themselves.
That being said, are you aware of any web services that offer encrypted file sharing, without installing a new app on a PC?
Whatsapp includes end-to-end encryption of messages and attachments. You can use the Web version to use it on your computer.
“Zippedfiles.zip” is not an “obscure” filename (in fact, it’s a perfectly logical one).
From a would-be snooper’s viewpoint, however, it is a completely unhelpful one. :)
One definition of “obscure” is:
“to prevent something from being seen or heard:”
Obscured might have been a better choice of words, but when something has been obscured, it is obscure. :-)