Hide from prying eyes.
A VPN, or Virtual Private Network, is one approach to securely connect to a remote resource. Depending on the VPN, that privacy can extend from one end of the connection to the other, or it can protect you only for a certain portion.
I’ll describe the different scenarios, and how you are — and perhaps are not — protected by a VPN.
Become a Patron of Ask Leo! and go ad-free!

VPNs encrypt and protect your connection throughout the entire path between your computer and the VPN provider’s server. Other forms of encrypted communication leave traces of your activity or don’t cover the entire distance. The WPA encryption used in Wi-Fi encrypts data only between your computer and the local access point. HTTPS connections encrypt data between your computer and the service to which you are connecting; your ISP can still see the service you’re connecting to. HTTPS over a VPN provides the most completely effective security.
No VPN at all
I’ll use this scenario as the base: you’re at an open WiFi hotspot, connecting to a remote resource like your email or your bank.
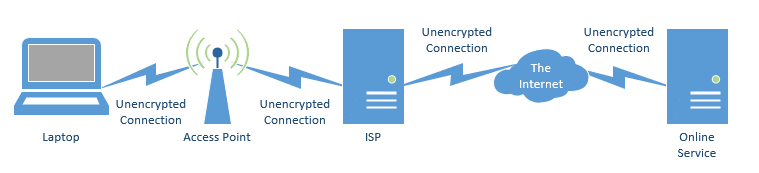
All the connections are unencrypted. That includes:
- The connection from your laptop to the wireless access point (aka hotspot).
- The connection from the wireless access point to the ISP (Internet Service Provider) providing the internet connection.
- The connection from that ISP to the rest of the internet.
- The connection to the specific service you’re using.
The largest area of concern is the connection from your laptop to the WiFi access point. That open WiFi signal traveling through the air can be “sniffed” (or read) by anyone in range with a laptop and the required software.
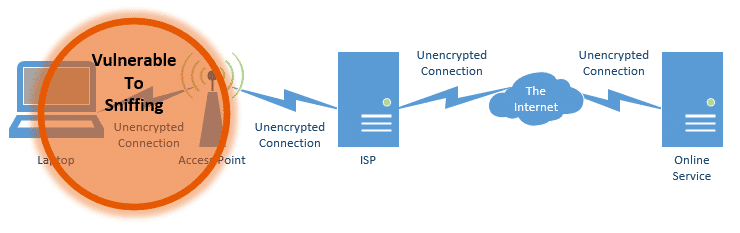
Lately, however, there’s been concern about the fact that your ISP can monitor what you’re doing. Specifically, they can see every remote site or service you connect to, and examine all unencrypted data you exchange with those servers.
WPA encryption
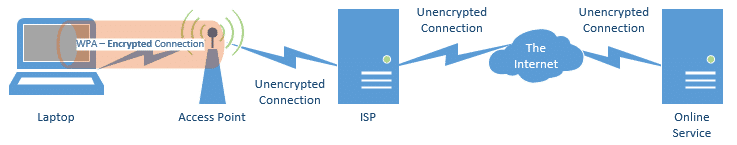
The traditional approach to protect yourself from open WiFi sniffing is to use the WPA1 encryption built into WiFi.
This secures the path between your computer and the WiFi’s access point. Hopefully, it’s how your home WiFi is configured, so as to prevent nearby homes or others from connecting to your WiFi, and through it, to your network, without the appropriate encryption password.
There are problems with using WPA.
- Most open hotspots at coffee shops, airports, and elsewhere don’t use encryption; the password requirement would confuse their customers more than it’s worth. That’s why these hotspots are called open.
- When WPA is used, it protects only the connection between your computer and the WiFi access point. Everything past that point in the diagram above remains “in the clear”.
That last point is important, because all the traffic is visible to the hotspot’s owner, should he or she care to peek, and to the internet service provider to which that hotspot is connected.
A VPN service
To protect yourself further, a VPN is a common solution.
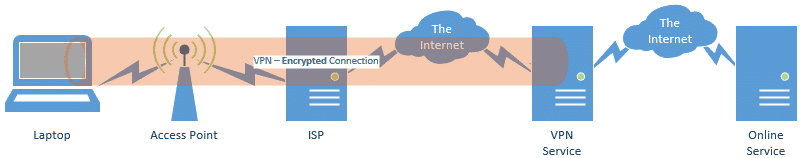
A VPN securely encrypts the entire path from your computer to the VPN provider. No one along that path can see your data: not other WiFi users, not the people managing the hotspot, and not the hotspot’s ISP.
For open WiFi or other situations with questionable security (such as connecting to the internet at a hotel), a VPN can be a great solution.
But it’s not perfect.
There are some things to note.
- The connection is only secured up to the VPN’s servers; the connection from the VPN provider’s servers to the final destination is once again unencrypted. That means the VPN provider, as well as any other networking equipment along the rest of the way, may be able to see your data, and can at least see which servers you’re connecting to.
- You’re adding steps between your computer and the server you’re accessing. The practical effect of this is that your connection becomes slower. How much slower varies based on the VPN service you use, their capacity, and the servers you attempt to access.
- Not all VPN services support all protocols. For example, your web browsing might work, but your attempts to use BitTorrent might not.
- Not all remote servers allow connections through VPNs. One non-security-related reason to use a VPN is that it can make you appear as if you’re located in another country. As a result, many services — such as streaming video services — block connections that use VPNs.
- Not all governments allow VPN connections to services based in their countries, so as to effectively censor what their residents can view.
Using a VPN, the ISP you’re connecting through can’t see that you’re using BitTorrent (for example), but the VPN service can. Your ISP would still see that:
- You’re using a VPN (and which VPN service you’re using).
- You’re sending and receiving an awful lot of data.
End-to-end encryption
True privacy is achieved with end-to-end encryption. Unfortunately, that isn’t possible in many cases, since it must be supported by the service to which you are connecting.
HTTPS is end-to-end encryption
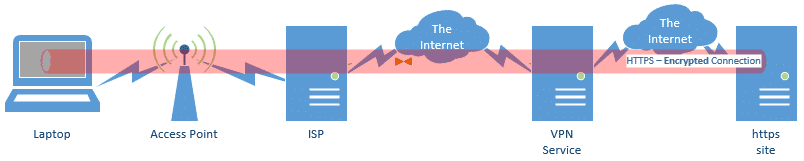
Connections you make via HTTPS are completely encrypted along the entire path from your machine to the remote server you’re accessing. That’s why banks (and other services that allow you to access sensitive data) should use HTTPS . Most web-based email providers also provide full HTTPS connectivity. In fact, more and more sites — including Ask Leo! — are switching to support HTTPS .
Similarly, when configuring a POP3, IMAP, or SMTP connection in your email program, if your email provider supports it, choose SSL or TLS. That’s the underlying encryption protocol used by secure connections like HTTPS. That way, your email uploads and downloads — as well as your log-in information — is completely encrypted along the entire path to your mail server.
Note, however, that even when using HTTPS, your ISP can still see which sites you connect to. Only a VPN can hide that information from them.
HTTPS over a VPN?
Just to complete the picture, if you’re using a VPN, and you connect to an HTTPS web site, your data is doubly encrypted for part of the trip.
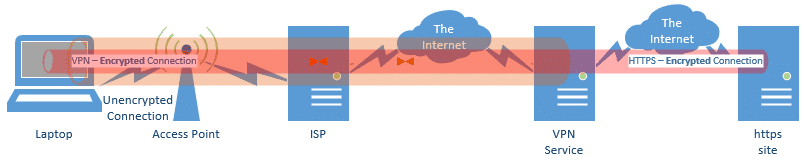
- The VPN protects your data between your computer and the VPN service.
- HTTPS protects your data between your computer and the service to which you’re connecting.
There’s really no practical harm. One benefit is that the VPN prevents your ISP from seeing which site you’re connecting to.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!



“That means that connections you make which use https are completely encrypted along the entire path from your machine to the remote server you’re accessing.” So is it safe to use a public wifi spot for internet banking?
04-Dec-2010
For the most part, yes. The data that is sent from your computer, through the hotspot and to the bank servers, and vice versa is secure. Beware however that someone else also connected to that hotspot is able to “see” you. It is possible for them to install software which allows them to see what you are typing. They could use that information to see your bank information.
Great article, with clear diagrams. I had previously thought VPN provided the same protection as HTTPS, but now realize the difference. Thanks!
Clarifying email security: What Leo said about SSL for email is true, but a bit misleading. This type of secure email is only secure between you and your email server(s). It is not end to end security.
For example, when sending email with SMTPS it is only secure between you and your SMTP server. The transfer of your message to the POP/IMAP server of the recipient is not secure. The transfer of the email from the recipients POP/IMAP server to the recipient is also not secure (unless they use secure webmail).
To Michael Horowitz… let’s say you use Hotmail with TLS for SMTP and send to a recipient that supports TLS (maybe another Hotmail user)… we know you are on an encrypted port to the sever (different than truly encrypting the message btw,) but I believe you have a shot at the email making it ALL the way to the recipient “securely” if they support TLS. But I don’t know… I don’t know if after the email reaches the server it doesn’t change from the encrypted port to 25 and then off to the recipient. I have written people about this (even web based email companies) but nobody ever answers…
08-Dec-2010
Thanks for your comment… I was actually the one who posted the link below a few weeks back when you were talking about encryption… I thought it might be misleading if it wasn’t revealed to the user/reader the “full” story regarding the difference between using an encrypted port (SSL/TLS) and encryption of the actual email (PGP, etc)…
http://luxsci.com/blog/the-case-for-email-security.html
I only care about encryption over the network – that the email is protected during the sending process… We know we can achieve that using SSL/TLS to the server – but from the server to the recipient is what is in question… if they also have SSL/TLS enablement – I am hoping it is “encrypted” during the entire sending process – from server to server… That is what I am trying to figure out…
Once again, thanks for taking the time…
09-Dec-2010
Check out:
https://www.eff.org/https-everywhere
It provides a Firefox extension which aims to automatically use https encryption for every website that offers the functionality, but doesn’t turn it on by default (and there are a lot of webmail programs that do not).
My own concerns were somewhat heightened a few weeks back when a different Firefox extension came out that was able to pick up any unencrypted login cookies from the network you were on – this includes both Hotmail and Facebook login information.
09-Dec-2010
Maybe I should be more specific… most credit card statements are done paperless now – if a thief or sniffer can get your username and password – see what credit card is being used – he/she could start pounding away and “guessing” the rest of the numbers and try to make fraudulent purchases. In the last 5 months I have had 2 credit cards taken by fraud even though I have never lost my wallet. This has led me to look further into email security like SSL/TLS.. doing what “I” can to ensure my incoming/outgoing is secure. Of course part of that is never using the first part of your email as a username and making sure your passwords are different. But even in doing ALL of this, hit twice in a year.
I know I’m answering a 6 1/2 year old comment, so this is for the benefit of others. Although it is possible to sniff out credit card numbers, use of SSL (HTTPS) connections should in the extreme majority of cases protect the number from being sniffed. Credit card number theft is most often done in places where people take your credit card in their hands for processing. They can copy or memorize the number and security code on the back. I’ve had 2 fraudulent charges against my credit card. I believe one was from a restaurant and the other a gas station which used carbon paper receipts. After that, I scratched off the security codes and keep them encrypted on my computer.
Another exemplary article Leo, it clears the security while data is traveling.
I use Thunderbird to access my email accounts. I will be staying at a hotel with free wifi. Will my email account be vulnerable if I use it there? How can I find out if my Thunderbird installation is using encryption? Thanks!
This article discusses that:
https://askleo.com/can_hotel_internet_traffic_be_sniffed/
If your account configuration uses SSL for both POP3/IMAP and SMTP, then you’re good.
A downside of VPN
I was doing a Google search with the VPN enabled in Opera (while technically not a true VPN, but for this example the results are the same as with a real VPN, and I got the following warning along with a CAPTCHA:
“Our systems have detected unusual traffic from your computer network. This page checks to see if it’s really you sending the requests, and not a robot. Why did this happen?”
Websites can determine that they are being accessed by a VPN (usually because of a large number of visits from the same IP) or a VPN shows up as unusual activity from your account as it jumps from country to country, as in this example. This can be disconcerting for the casual user who simple wants to protect their privacy from their ISP or their location from the websites they visit. This isn’t to say, don’t usea a VPN, just be prepared that it’s not a simple plug and play that you install and don’t have to think about.
In this annoyance (CAPTCHA test) also lays proof that we ARE VERY anonymous!!
You see, VPN providers not only hide our real IPs and provide us with one of theirs, but through “shared IP technology” they share the masking IP amongst MANY of the customers at the same time. For example: if I use my VPN server in Atlanta Georgia, and it assigns me IP “123.222.333.444” that number is presumably unique to me.. but it is not. It gets assigned to multiple customers at the same time. So my first layer of security is that it will trace back to my VPN, and not me. And the 2nd layer of protection is if the VPN were forced to identify the user of 123.222.333.444, they would respond with: “here ya go, we had 50 clients using that IP simultaneously. We don’t know which one went where…”
So when we 50 common IP users use Google 2 or 3 times each, that adds up to 150 queries. Google starts to suspect robotic activity from 123.222.333.444, so it throws a CAPTCHA at us. Part of the price of peace of mind!
All of the VPN users may share an IP number which is visible to the websites they visit, but the the users connect to the VPN through their real IP number, so if they are forced to give up that IP number to authorities, they have it to give.
IF (and only if) the service kept logs. Many make the explicit statement that they do not.
Does a VPN running on a server protect the server from incoming traffic (i.e. port sniffing)?
Not really, as I understand it.