Use it to keep hackers out.
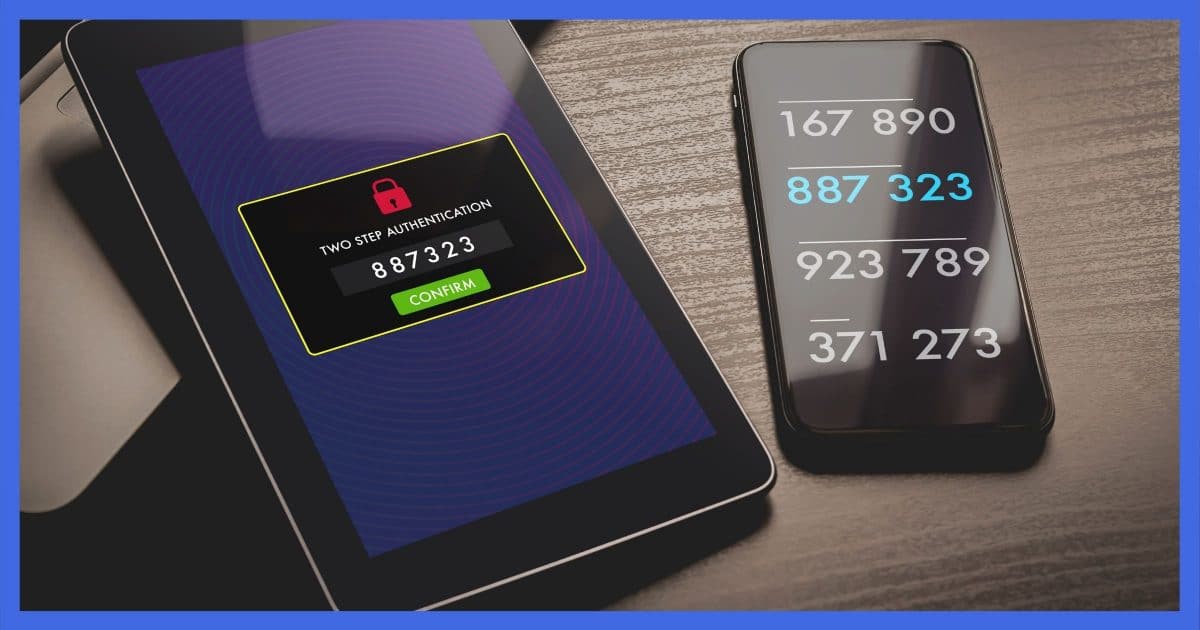
We rely on passwords to protect our online security. At the same time, hackers seem to be getting better at figuring them out!
In response, security folks created something called “two-factor” or “multi-factor” authentication, which uses two different types of information. Both must be correct to prove you are who you say you are and give you access to the account.
It’s something I strongly suggest you use. Two-factor authentication keeps your account secure even if your password is compromised.
Become a Patron of Ask Leo! and go ad-free!

Two-factor authentication adds something you have — like a mobile device — or something you are — like your fingerprint — to something you know — your password — to confirm you are authorized to access an account. There are contingencies for losing your second factor, as well as ways to make two-factor less intrusive in day-to-day use. Even if they know your password, hackers can’t get in with two-factor enabled. This is how two-factor authentication keeps you secure.
Authentication
The word “authentication” gets thrown around a lot.
All authentication means is proving that you are who you say you are. It validates you are authentically you, not some impostor (or hacker).
It’s important because once you’ve proven you are who you say you are, you get the right to use the things that are yours. Once you prove you are you, for example, you’re allowed to access your email account.
In person, we use physical things, like a photo ID, to prove we are who we say we are. Online, things are more difficult.
What you know
Authentication has almost always been in the form of something you know. You know your username and the password that goes with it. Since only you should know your password, your ability to type it in proves you must be you and no one else.
If you forget your password, the answers to a set of security questions might be used instead, which still boil down to something(s) you — and hopefully only you1 — know.
Something you know is easy to transfer from one person to another. When it’s on purpose, that’s okay, albeit it less than secure. When someone who shouldn’t know your password learns it, something you know becomes something they know, too. The result? They can impersonate you, too.
What you have
Two-factor authentication typically adds something you have to how you prove you are you. When it comes time to authenticate, you need two things:
- Something you know: you must know your username and the password that only you should know.
- Something you have: you must possess something specific that is also completely unique to only you.
How you go about proving you have something in your possession is pretty hard to do securely — until you factor in encryption. For example, “what you have” might be a smartphone running an application that has been associated with your account using encryption. More on that in a moment.
What you are
There’s an additional factor sometimes combined with a password, and sometimes even a password plus something you have:2 something you are.
Most commonly, this is biometric data like your fingerprint or your face, each of which is, in theory, unique to you. When it comes time to authenticate, you need two things:
- Something you know: you must know your username and the password that only you should know.
- Something you are: you must provide your fingerprint or allow a facial scan, those things again being completely unique to you.
Fingerprint and face ID are fairly common of late, though it’s generally used by itself as a single factor. Only when combined with something you know and/or something you have is it considered multi-factor.
Proving what you have
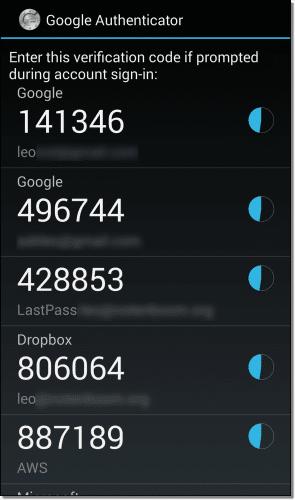
The most commonly recommended tool for two-factor authentication is the Google Authenticator app.3 It works like this:
- You install the Google Authenticator app on your smartphone.
- You “associate” the Authenticator with your online account. This is usually done by scanning a QR code provided by the set-up process for that account, or by entering a code that’s displayed.
The app now begins displaying a six-digit random number that changes every 30 seconds.
In reality, the number isn’t random at all — it’s a complex function of encryption keys created as part of the process you just completed. It’s completely unique to your account and your smartphone. Only the app and the service know what the number should be at any point in time.
If you can type in the correct number provided by the app when requested by the service, it proves you have the device running the app.
In this case, your two factors are:
- Something you know: the username and password to your account, which you prove you know by typing in as usual.
- Something you have: your device, which you prove you have by entering the number displayed by the Authenticator app when requested.
Your log-in process now requires you to provide your username and password, and then provide the random number currently being displayed by your smartphone. Either one by itself is not enough.
Using SMS for two-factor
An alternative (for those who don’t have a smartphone or who just prefer it) is to use text messaging (SMS) to prove you have your phone.
Set up is simple: you give your mobile number to the service and tell them you want to use it for two-factor authentication.
Your two factors are:
- Something you know: the username and password to your account, which you prove you know by typing it in as usual.
- Something you have: your phone, which you prove you have by entering the random number text-messaged to it when you try to log in.
Your log-in process now requires you to provide your password and the number texted to your phone.
Some systems can use automated voice readout of the number, meaning you don’t need to use texting at all; you don’t even need to have a mobile phone — a landline will do. When you try to log in, a voice call is made to your phone number and an automated system reads you the number you need to type in.
While there are occasional stories of SMS being hacked, the reality is that using SMS two-factor is still much more secure than not using two-factor at all.
Making two-factor less annoying
“You mean I have to do this every time I log in?”
Nope.
After you log in once using two-factor authentication, most services let you set how often the second factor will be required on that device. You usually have the following options:
- Never again on this computer. This means this computer is trusted. You can log in on it again without needing the second factor. (Note: clearing cookies usually resets this per-browser setting.)
- Every-so-often on this computer. This usually means the service will not ask for a second factor again for some number of days, often 30. (Note: clearing cookies will reset this, too.)
- Always ask. Two-factor authentication is always required.
This lets you tailor exactly how aggressive two-factor authentication should be.
On a computer at home, you might never use two-factor, but on a mobile device or laptop you travel with, you might require it always be used in case you lose the laptop. This is exactly what I do.
Two-factor protects even if you enable and never use it
“Why would I choose ‘never ask again’?”
“Never ask again” can apply only to a computer on which you’ve successfully used two-factor at least once. On any computer you’ve never used, two-factor will always be required at least once.
That means the computer of a hacker who has stolen your password can’t be used to get in.
This is how two-factor authentication keeps you secure: Even if they know your password, hackers cannot log in if you have two-factor authentication enabled.
Losing your second factor
“What happens if I lose my phone?” (Or other two-factor device).
When you set up your account with something like Google Authenticator, you will also be given a set of one-time passwords or recovery codes. Save those someplace secure. You can log in with each of those passwords exactly once without requiring your second factor.
 After losing your second factor, you would:
After losing your second factor, you would:
- Log in using a one-time password.
- Temporarily disable two-factor authentication.
- Change the password for safety (optional, but recommended).
- Re-enable two-factor authentication, associating a new phone or another two-factor device.
I save the one-time passwords in an encrypted file.4
Some services, like Microsoft, will also let you set up a recovery code independent of two-factor authentication. I recommend you do that, too.
If you’re using SMS as your two-factor mechanism, recovery can be as simple as going to your mobile provider and getting a replacement phone while keeping your mobile number. Texts are sent to your mobile number and will follow you to your replacement phone.
Two-factor availability
I have two-factor authentication enabled on all of my accounts that support it.
For me, that means, among other things, my bank, Amazon, Gmail, LastPass, Dropbox, Facebook, Evernote, Microsoft, TeamViewer, and even my World of Warcraft account.
Unfortunately, not every service supports two-factor authentication. I strongly recommend you consider it for all your accounts that do.
You’ll also find that in addition to or instead of the two common methods I mentioned above — Google Authenticator and text messaging — several services also have other approaches to two-factor. Facebook allows you to use the Facebook mobile app to provide the code. Some services provide keychain fobs that display the randomly changing number. Other services use devices like the USB-based YubiKey.
Pick what makes the most sense to you, but add two-factor authentication to increase the security of your most important accounts, if not all of them.
Do this
Subscribe to Confident Computing! Less frustration and more confidence, solutions, answers, and tips in your inbox every week.
I'll see you there!
Podcast audio
Footnotes & References
1: Since we’ve made so much of our information public in recent years, these questions have fallen out of favor. Too many other people might be able to discover the answers to your so-called “secret” questions.
2: Resulting in three-factor authentication. This is one of the reasons you’ll also see this enhanced security referred to as “multi-factor”, to cover the possible combinations.
3: Or the compatible app, Authy. Authy can be installed on multiple devices, allowing any to be used as your second factor.
4: This is an excellent use, for example, of the secure note feature in many password managers — with the exception of the one-time codes for the password manager itself, of course.





It’s very worthwhile exploring the related articles and not just assuming the current practice of Secret Questions have got you covered as the 2nd step of verification. Secret Questions are a pretty weak method of security as the Secret Answers are frequently known by friends, family, work and class mates.
Though Leo has a creative way of making Secret Answers more secure for those sites that only have Secret Questions.
I’m finding that secret questions are, thankfully, falling out of favor. Many sites that used to have them have replaced them with other forms of validation.
As long as a system created or understood by humans is relied upon, another human or machine created by a human will eventually crack it. Trying to type a bunch of letters and numbers is really too easy and then they want you to do a ‘Turing’ exercise and choose items that have the same characteristics that can really be frustrating if you can’t really get a grip on their concept or see it well…those aren’t even useful for the handicapped.
The answer hasn’t been thought of yet because they are too busy trying to see if you are AI.
Secret answers stink, but there’s an easy way to make them safe if you can’t avoid them : use a long, random password as an answer whatever the question, and save that in a password manager (in Kee Pass : create a custom field for it under the Advanced tab.)
Unfortunately, secret answers are aimed at precisely the type of people who wouldn’t be using a password manager, and wouldn’t be comfortable with one.
The article explicitly mentioned your suggestion. 🙂
I live in India, but travel to the U S once in a while since all my children are settled there. I am hesitant to activate the Google two factor authentication because my Indian phone does not work when I am in the U S. What would be the preferred option in such a case.
If you use the google authenticator app on your phone it should work. The app does not require connectivity or phone calls, it’s just a program that runs on the device.
“It’s just a program that runs on the device.”
A fundamental point, which is not stressed often enough. I had trouble understanding it, and I still forget it occasionally.
Google will allow you to pre- download ten codes that can be used when you travel. The codes are only used one time and then you need to go on to the next.
BTW: YOU CANNOT USE EUDORA WITH TWO PART AUTHENTICATION! Eudora only allows one password – no codes! Then Google blocks the attempt to download your gmail!
I believe you can use Eudora and other email programs that can’t do two-factor by looking for and setting up “application passwords”. Check the Google options for that.
I was wondering about just having a landline and that is it. Are you just out of luck on all of this…
There are some services which offer the option of the authentication by voice message. Those should work with a land line. Unfortunately, most websites don’t to that.
Thank you Mark Jacobs.
FB requires a mobile phone. i tried to use my land line for two factor and FB has SMS only. i`m deaf and have an automatic caption phone. FB two factor will not work for me. i`ve written them about it but without a premium account they won`t answer me.
I’d love to know why they think we all have cellphones anyway. Some of us care to eat and live in a house.
Depends ENTIRELY on the online service you’re talking about. As I mention in the article, SOME will actually read you a number over a voice line.
Leo, this problem first showed up today on your newsletter page: an annoying pop-up on the left edge of the page that gives me a “choice” to share with facebook, twitter, etc. It covers part of the text that I am reading. Is there a way to get rid of it?
That sort of a thing on a web page is usually put there by the web designer. I would think that maybe Leo is asking us to help share his page. So I’m going to click it and share the page when I like an article.
I will be adjusting the left margin as soon as I can. (I’m on the road.) Connie’s comment is spot on – sharing is one of those things that’s pretty critical to Ask Leo!’s survival. I’ll work to make it less annoying.
That should be fixed. Please let me know here: http://askleo.com/ask if it is not.
I was having this problem a while back and it was corrected enough to read the article content by reducing the zoom to no more than 100 %.
I. Kertesz – Answer: I use Firefox as my main browser. I installed an add-on called “No Squint” which makes web page font larger or smaller. Normally I have it set for very large web page font. I had the same problem you did. The pop-up on Leo’s page blocked the wording. I had to use No-Squint to reduce the size of the font since I could not delete the annoying pop-up. Once reduced the font I could then read it.
The bar can be removed by clicking on the arrows that appear beneath it when you hover over it.
My wife and I have cell phones through AARP. No text. No internet. Voice only. The company is Consumer Cellular. Two phones – Two people – 600 shared minutes: Total price = $35.00 per month! There should be a way for two-factor authentication to work without the use of smart phones. Some of us are retired and cannot afford smart phones.
Most 2 factor authentication sends a normal text message which should work on any cell phone. Some even offer the option of a voice message which would even work on a land line.
And some services DO do two-factor authentication – as mentioned in my article – by calling and speaking the security code to you.
You might check out TracFone. I’ve had their service since March. Depending on how many minutes you use, you can end up easily with two accounts under $35/month combined, and have access to phone calls, texts and internet. I got this phone:
LG Optimus Dynamic II – LG39C – Android Prepaid Phone with Triple Minutes (Tracfone)
and prepaid a year of service at tracfone.com. When you check them out, be aware that when you have an ANDROID phone like the LG I gave you the link for above, you get TRIPLE the minutes that are listed on the card you get at Walmart or other stores, or various offers online, and that’s that number of minutes phone call, that number of text messages plus that number of megabytes of data.
Do check it out. I am still very satisfied, but at 63, I don’t make a lot of phone calls, but I love the texts that Amazon sends me to tell me when packages should be delivered. (And if you add a new card before your “x” days of service runs out, all of your accumulated minutes, texts, and megabytes that you haven’t yet used carried over to the renewal period, plus triple the number that you just added.
My first cell phone was a TracFone. It was just for emergencies. When I finally had an emergency there were no minutes left to use. You not only used minutes by using the phone, you lost so many minutes a month by carrying it around in your pocket or in your glove box. I don’t know if they still do it that way now a days.
I. Kertesz…………..I just noticed that there is a double blue arrow at the bottom of the pop up. Click on those arrows and the popup will disappear.
Thanks for pointing that out. I wish they were permanent and a little more obvious.
p.s. to content reader, my prior comment was not a comment on your article, but on the one user’s AARP phone comment.
John
Hi Leo,
The two factor authentication has really saved my gmail account recently. One night, I kept receiving the codes for my gmail account (5 times). Then, it stopped. As my wife and daughter sometimes open and read mails, I thought one of them should have opened it. My wife was with me at home, my home computer has not been in use, and my daughter confirmed Not having opened my mail a/c. Obviously, my password has been stolen. I immediately accessed my account and changed the password (tougher). As of today, my account looks safe.
I wanted to thank Google for it, but it is difficult to find a Mail ID for it.
Shanker, click on the gear icon in the upper right then click send feedback. you can thank Google that way. you`ll only get an answer if you have a premium account.
I’m probably not understanding something or just not thinking it all the way through. What if someone STEALS your phone. They now have access to both factors. They have access to your email and your text messages and your phone calls so TFA no longer helps you stay secure, correct? Again, what am I missing? I have a passcode on my phone.
Right. If they hack your password, AND steal your phone they can get in. Those are two separate things, however. Given that most hackers are very, very far away from you (typically overseas) the likelihood of them having stolen your phone is next to nothing. 2FA remains incredibly robust.
In South Africa there have been cases where hackers, who have obtained a password to a banking account protected by 2FA, have been able to obtain a replacement SIM card linked to the victims cell phone (as part of a replacement SIM process). The the victim’s cell phone then goes off the air as it’s SIM has been deactivated while 2FA text messages go to the new SIM card (which is in the possession of the attackers).
2FA is better / stronger than single factor authentication but it is still vulnerable to attack.
In the case of a lost or stolen cell phone a “remote wipe facility” is strongly advisable. There is just too much personal data on them and every app adds to the attack surface available to a hacker.
Remote wipe is important, I agree. I need to write that up. FWIW I use https://preyproject.com on my mobile devices.
Something still seems odd and stupid, at least in some scenarios.
Eg., Amazon. I’ll log in, on my phone, and they send me a text on that same phone.
Now, I get it, that the hacker/thief, exfriend, whatever should not have the passwords. But it still somehow seems mentally off base to send that information to the same place you are attempting to log in at.
Also, I think I am missing something about password managers; in theory they seem wonderful. But in (probable reality) are they? It does not seem safe to use the “cloud” to store passwords. And yes, when it comes to online, I make extreme paranoids seem quite oblivious to security issues.
Sending the confirmation to the same phone isn’t a security breach. You are logging on via the Internet and the confirmation code is sent via SMS text. A hacker with your phone would have to know both your phone’s password and the email address and password of the site login so it’s still two factors.
Password managers are safe as long as the password manager uses good encryption and you use a long strong password to protect your password vault. If you don’t trust the cloud, KeePass only stores your vault locally and not on the cloud.
Mark’s spot on. Put differently: if the hacker has both your phone and your password he has both factors. This same scenario would play out regardless of what form of two factor authentication you use — if the hacker happens to get their hands on both factors, then they can get in. The great thing about the phone is that you can instantly disable it with a call to your mobile provider.
If they steal your phone, it’s not likely that they will have your passwords unless you have them stored unencrypted on your phone.
OK. Thank you Leo and Mark for the reply. I just wanted to make sure I understood. I’m just too paranoid (with a touch of lazy)…so now I’ll enable 2FA on my google account, given the recent reports of Mail.ru, Yahoo, Hotmail, and Gmail being hacked.
http://www.forbes.com/sites/bensin/2016/05/05/if-you-use-gmail-hotmail-or-yahoo-mail-you-should-change-your-password-now/#7a54a93f683b
It turns out that the report is based on incorrect information, but it’s a good reminder to keep passwords secure and consider 2FA anyway.
Initially I resisted 2FA mostly because I didn’t understand how it worked. I used to think “if I lose my Android I won’t be able to access my accounts”. Once I made the effort to see how it actually worked I was hooked. I’ve been using 2FA for various accounts/services that support it for a couple of years now and wished I had made the move sooner.
I also use LastPass for password management and keep a copy of my passwords in a volume encrypted by TrueCrypt. The master passwords for LastPass and TrueCrypt are memorized. I also have a physical copy in a safe place. With respect to my home PC, I never choose the “trust this device” option – I always want that SMS sent to my phone. It can be a pain in the you-know-what but then I consider the alternative – I suffer a break in while I’m away and that PC goes missing.
Authy is a great 2FA app that can be downloaded to pretty much any device and your desktop. I find it to be a great service.
https://www.authy.com/
Banks and credit card companies usually offer the options to send you an email or a voice message, or have you call a number yourself to get the confirmation code. Very helpful for those like me who work from home and don’t have cell signal at home. 2FA that only works with text messages is useless to me most of the time.
To be clear, not all banks offer all those options. Indeed, not all banks even offer 2FA.
In Europe, all banks not only offer 2FA, they insist on using it. I wish the US would adopt that policy.
I don’t even have a cellphone, I can call the bank and find my information with the automated system or talk to a banker live and I just get my cash out and pay for it directly or purchase the transfer method required.
No muss and no fuss, no Mr. In-between.
Hasn’t NIST said that SMS as 2FA is not secure?
That’s true, but it’s my understanding that this disrecommendation of SMS as a second factor is more relevant for governmental agencies and businesses which might be specifically targeted. For the average user, the odds of someone hacking into your SMS communications is next to nil.
Yes, No, and Not exactly. While it’s technically spoofable, using it is still much more secure than having no two-factor at all.
My Mobile phone has access to my Google account so I can view my Emails and calendar. I gave it this access a long time ago and I am never asked for re-login details. The phone does require a 4 digit switch-on code
Now, If my mobile is lost or stolen what is stopping a finder/thief from:
* browsing to any banks web site and trying the following…
* entering my email
* asking to RESET the password
* receiving the password on the mobile phone
* using the email & reset password details to log in
* Receiving the 2FA code by sms
and accessing my bank accounts.
( I refuse to do banking on my mobile, but if I did use banking apps or web browser surely this would make it even easier for a finder/thief?)
In England from 14 September 2019 banks insist on using 2FA, and “want” to send sms messages to my phone.
My instinct is that this is all terribly insecure – even with 2FA
what do you think?
Regards
Mark
I was on holiday, inexplicably forgot my mobile password – hardly turned off- went to Yahoo. I’m abroad so two step authentication kicks in. Can’t respond because locked out of phone…second option; use alternative email…gmail. Went to gmail. I’m abroad so verify two step authentication on mobile…. CATCH22. Solution. Very, very easily, can’t quite believe it. Got my PUK digitally. Freed up phone and all sorted. Got home undid two step verification. Why bother when you only have to phone the company and without any checks you can get your PUK
Reading the feedback, I see I am only one of many who has had problems with 2FA while travelling abroad. With an local country SIM card in my phone, I couldn’t receive 2FA security codes via SMS or voice call. The issue was getting funds from my bank – a large bank with international branches. After returning to USA, the bank’s response and suggested work arounds were so bad I have dropped the bank after more than 20 years a customer.
The solution, my new (mainly online, few branches) bank also will send security codes via email. I can retrieve the code through webmail on my phone, then proceed. Email is probably not as secure as SMS, etc. . . . . but as LEO says, it is better than no 2FA at all.
“Never again on this computer” : this is pure genius, and the first time I’ve read about it. I read tons of articles on 2FA, and have never seen this mentioned once.
It could be a game-changer for me, because I use a desktop computer and an always-off smartphone. I only use the latter as a pocket computer and an outgoing phone for rare calls. The long boot time and multiple passwords needed to start the phone make it really impractical for me to use cell phone-based 2FA.
Unless I can use “Never again on this computer”. However, I have never seen this option explained by services offering 2FA. Whether it is because they don’t have it, or because you’re not informed of it until you set up 2FA, I don’t know.
Other points I feel should be mentioned when recommending 2FA :
1. Making backups of secrets. Recovery codes are good, but they depend on the service. Not all services might offer them. One can, and should, do one’s own backups by saving the QR code or the relevant character string.
Am I correct in assuming there’s one secret per service where 2FA is enabled, as opposed to one secret per authentication app ? This is never made clear in 2FA articles.
2. 2FA by SMS is obsolete and dangerous because of SIM-swapping. SIM-swapping is big in the United States. Notably through corruption of phone company employees, which you can’t prevent. I haven’t heard of it happening in Europe, but you never know. Cases have been found in Africa and Brazil.
1. A new secret is generated each time you pair the app with a service. (And yes, I agree, capturing the QR code is one way to save yourself from losing the device, or allowing more than one device to be used.)
2) SMS two factor is still better than no two-factor at all.
Hmm. Just a thought. 2FA by SMS creates metadata where there previously where no metadata. Eavedropping on a mobile phone these days is extremely easy. You don’t even have to get your hands on the phone in question. I’m beginning to wonder if we are lured in to an extremely effective eavesdropping society under the pretext of improving security, when we in fact are doing the opposite??
I think the whole issue of SMS hacking in relation to multi factor authentication is overblown. For someone to catch a text message with a 2FA recovery code, the hacker would need to be in proximity to the phone and know that an account recovery code is being sent to that phone. It’s probably just as statistically infeasible as cracking a long password by brute force.
I’ve been a Yubikey user for about six months now and love it (once configured, which is *not* straightforward). I did come across an issue lately with physical 2FA methods like this: tablets and phones. For example, my Samsung Tab 4 tablet only has a micro USB port. Using an adapter, it does not acknowledge the Yubikey, making it impossible for me to sign into Gmail (creating an app password doesn’t help with 2FA enabled — tried it). An important FYI to others that I stumbled across.
My solution is to make sure you have additional 2FA methods also enabled. Generally GMail offers alternatives if you can’t use one. I’ve had the YubiKey experience myself, but I could fall back to the Google Authenticator method, because I also had that configured.
Great point! Not sure why I didn’t think of that. Just implemented Google Authenticator and I’m in. Thanks!
But couldn’t one argue that by enabling additional 2fa besides the YubiKey, that it somewhat defeats the purpose of a YubiKey secured account since your 2fa is only as strong as the weakest link? ; because to my knowledge the YubiKey option is THE most secure form of 2fa on Google and by enabling weaker forms of 2fa (like Google Authenticator etc), it could potentially bypass the high-security of YubiKey.
but for those using YubiKey… it’s always best to have a minimum of two YubiKey’s tied to your Google account as this way if you lose your primary YubiKey, one can use the backup YubiKey to gain access to the account and then one can simply remove the lost YubiKey from their Google account and then buy another YubiKey and register that and you now have two YubiKey’s tied to your Google account once again. because while only having one YubiKey on your Google account will technically work, if you happen to lose that YubiKey or it gets damaged etc, your probably permanently locked out of your Google account which is why it’s always best to have a minimum of two YubiKey’s on your Google account to help ensure this scenario does not happen to you. NOTE: one should always keep the backup YubiKey stored in a secure location as this way if you happen to lose the YubiKey you typically use, you won’t be locked out of your account.
NOTE: YubiKey works on Linux as one just needs the following file added to their “/etc/udev/rules.d” folder… github.com/Yubico/libu2f-host/blob/master/70-u2f.rules ; basically you just copy that text and paste it into a file named “70-u2f.rules” (without the “) and put/save that file into the “/etc/udev/rules.d” folder and reboot and YubiKey will now work on Linux. NOTE: I noticed if one is running their browser (Firefox or Chrome etc) in a Firejail sandbox that the YubiKey won’t work. but a temporary work around is to load the Firefox/Chrome browser like normal, log into your Google account etc with the YubiKey and then in the future as long as you stay logged in to your Google account etc, at that point you can close the browser and then load it back up through the Firejail sandbox and things will function like normal. but since I don’t think most people on Linux will run their browser through a sandbox, the YubiKey will function normally once you do the “70-u2f.rules” stuff I mentioned above and run the browser normally.
@ Reid ; personally I would just avoid using a YubiKey secured Google account on non-proper computer devices that don’t support standard USB port. so if one can’t use a YubiKey on a tablet etc, what I would do is make another Google account of lesser importance and simply don’t use the YubiKey on it and for the Google account of higher importance, use the YubiKey only on proper computers (i.e. desktop/laptop) which always have standard USB ports on them. I get this might not be optimal, but at least you don’t have to sacrifice optimal security on your most important Google account. so in short… with two Google accounts one can put all of their higher importance stuff on the account tied to the YubiKey and stuff that’s not as critical you can use on the Google account of lower importance without the YubiKey 2fa.
Technically, yes, but if it’s what makes people feel better about using two-factor at all, using multiple 2FAs is still better than no 2FA at all. Even the recovery code you set up when you enabled 2FA is a kind of additional 2FA itself. What do you do? You keep it in a secure place. If you want to use Google Authenticator as your backup 2FA, put it on a device you always leave at home. And so on. Again, it’s ALL better than no 2FA at all. And, of course, there’s no such thing as perfect security either.
I agree with your basic point and all (since that seems to be the general word that any 2fa is better than no 2fa at all among the experts). but personally… I can’t see spending $ on YubiKey’s and then pair a weaker 2fa with it is all as one would have been better off avoiding the YubiKey option in the first place since the whole point of using YubiKey is to make ones security as high as currently possible (articles online say this, “Google has not had any of its 85,000+ employees successfully phished on their work-related accounts since early 2017, when it began requiring all employees to use physical Security Keys in place of passwords and one-time codes”).
so basically… I would either opt for the full-on security with YubiKey or just stick to free 2fa options which are a bit weaker, but like you say, better than nothing at all. I can’t see mixing the two.
also, I am not a fan of using smart phones for doing anything sensitive online as if ones phone get stolen etc problems one does not need could arise, so I just eliminated that problem outright. so anything that requires a phone, I simply don’t use it. so while that may potentially open me up in other areas, if one is careful, you should be safe enough if your password is strong and one does not enter sensitive info into the web browser unless manually going to the official websites sign-in page instead of clicking suspect links in email etc that claim to be from a legit website as I think if people just got into the mindset that assumes any emails your not directly expecting to show up are asking you to sign in etc (or those ones that use fear to get people to react and click their shady links etc without thinking), to be a scam, that could eliminate a lot of problems by just getting people into a habit of that. even if someone gets a email from say Paypal that they think is legit, just manually go to the Paypal website and check on there instead of clicking on a link which could be shady.
but with all of that said… I suspect anyone reading password stuff etc on this site is already ahead of the average person in terms of their online security who probably don’t even use a password manager (especially given the effort of initial setup turns many away from using it) and is probably using the same so-so password on multiple accounts etc, which as we all know is a bad idea.
hell, I am sure my sister is so-so with her online security. but it seems a lot of people (which I would imagine she’s included) just don’t really care or think we are exaggerating when we say one needs a password manager etc until they get burned and their sensitive accounts get taken over, of which ones email tied to plenty of sensitive accounts gets taken over which can wreak havok on their online life.
While I disagree with a few minor points, I totally agree with the pragmatic, and sad result that many people need to get burned before they begin to take security seriously. You and I can preach as much as we like, but until people experience it, we’re often just preaching to an empty building. 🙁
Cell phone 2FA hacking is theoretically possible but doesn’t it take expensive equipment and can’t it only be used if the hacker knows the cell number of the phone used for 2FA. From all of the 2FA sites I use, the sites don’t include the phone number on the verification page. They sometime give the last 4 numbers of the phone number or a part of the email address or other times nothing at all. I still trust SMS second factor.
I assume you mean hacking cell phone 2FA. (In which case I agree. It’s still way better than no 2FA at all. In fact I seem to recall saying that somewhere: Why ANY Two-Factor Is Better than No Two-Factor at All. )
)
Yes I accidentally left out “hacking”. And I was thinking of that article when I wrote that. I also forgot to include the article link. 🙂
A TRUE HORROR STORY ABOUT 2FA:
I had 2FA set up wth PayPal and my Jitterbug[tm] flip-phone.Worked just dandy for a long time. I’d login with E-Mail and passphrase, they’d text me a 6-digit code which I then fed back to them, and I’d be in.
UNTIL…
Until, all of a sudden, PayPal either wasn’t sending the 6-digit codes any more, or else I wasn’t getting them for some reason. For over A MONTH, I was locked out of my PayPal account!!!
I was actually in the process of upgrading my flip-phone to a more advanced model, in the hope that that would solve the problem, when I decided to try with my old phone (the new one hadn’t arrived yet) one more time. As stupid as that sounds, it actually worked! Finally — I got their 6-digit code! I was in!!! Phew!!!
Very first thing I did — you guessed it! — was to very hastily turn OFF 2FA. “Not quite ready for prime time,” I said to myself with some regret. But really, I can’t afford to be locked out of my account like that!
But as I did this and logged off, something caught the tail of my eye. (“What did that say…? “)
So I logged back in (2FA -free) and took a closer look. What’s this about an “Authenticator App”…?
Long story short (yeah, I know — too late!), I ended up getting LastPass Authenticator (which, although it’s a tad glitchy on my year 2016, 6th generation, Amazon Kindle Fire HD8, nevertheless seems to work just fine operationally) and I now have 2FA enabled again!
I’m considering switching to Google Authenticator some time in the future — but for right now, I’m just going to leave things as they are and just relax, and savor the relief…
Phhheeeeewww!!!
I have an old Kindle Fire and find many apps are glitchy on it. That’s the fate of unsupported OSes.
I might recommend Authy as it makes it easy to have more than one two-factor device, and backups, in case you lose your phone. Also, set up multiple two-factor methods with the accounts (like Paypal). Though they should have had a way to get in to your account without it (usually with confirmation email, recovery code or whatnot). I will say that while Paypal was one of the first on the two-factor scene, they have consistently been the least reliable, at least for me.
UPDATE:
I’ve switched over to Google Authenticator v5.00, but I see no option for creating a list of codes in advance (which Leo mentioned as a backup in case you lose the Authenticator).
It’s still worth it, because when the LastPass Authenticator was first started, it very annoyingly popped up a notice (twice!) insisting that it requires access to Google Play in order to run (and then proceeds to run just fine without it!).
While you’d think that Google Authenticator, being a Google product, would have that same flaw, this is not the case: works perfectly fine without any complaints at all!
BUT, I’m thinking of switching again, this time to Verisign’s VIP Access. The newest version doesn’t work on my Fire, but I’ve found an earlier version that does; it’s drop-dead simple to use, and I really like its interface! My only worry is that this earlier version might be “out-of-date” in the sense of having been found to possess some vulnerability, and therefore no longer being recognized or accepted by online services.
I guess I’ll just have to wait and see…
I recommend Authy. It allows you to backup your google authenticator tokens.
The one time code is a function of yoru account, not the authenticator. For google go here: https://myaccount.google.com/signinoptions/two-step-verification and near the bottom should be “backup codes” — either an option to display them (which you should copy/paste to a secure location) or create them.
Leo:
“Though they should have had a way to get in to your account without it (usually with confirmation email, recovery code or whatnot).”
In point of fact, they did indeed have such fallbacks — for my passphrase. They did NOT work for the “two-factor.” I actually tried them and ended up with a brand-spanking-new passphrase (which I didn’t need!), but my SMS two-factor wasn’t affected at all. Why do you think it took me a month to get in?!?
To be clear, providers should have a contingency plan for a lost second factor. In fact I’m not aware of one that does not. You may have to set it up in advance (like traditional recovery emails, one time codes, or others). None involve getting a new password/passphrase.
My bank has moved to 3 factor authentication. First I enter the username and password on the website. Then to get in they send a TAN (Transaction Authentication Number, a one-time password) to my phone app. The third factor is entering the app password to see the TAN. To make a transaction, I have to enter the app password again to receive a second TAN. I’m so glad I have a password reader on my phone, otherwise I’d have to type in a lot of passwords and PINs.
Leo –
Hi. A bank recently implemented what seems like a form of Two-Factor Authentication. When you first try to access your online account, after entering your user ID and password, the bank calls your registered phone and provides you with a code, which the user then keys into the bank’s website. And then you’re in your online account. Typical 2FA processing so far.
What is different (for me, at least) is the bank will not call your phone every time with a code. They will call you with a code only if they detect a different IP address being used. So this bank appears to be using the computer, instead of the phone, as the “something you have” requirement. (I would like to force a phone call each time, but I can’t change my router’s dynamic IP address on demand.)
What are your thoughts on the bank’s usage of the IP address? Is it just as safe — or safer — to use the IP address rather than the phone as the second authentication?
Thanks.
It’s probably not the IP address, but a cookie. I’ll bet if you clear cookies (or use a different browser, or fire up in-private or incognito mode) it’ll do the phone thing again.
Very common, very convenient. The “what you have” is access to the phone at that number. That it remembers that it’s seen this computer before (typically by cookie, as I said) is a common convenience.
Leo, actually, it was the bank who informed me that a call from their system is triggered only if a different IP address for my device is detected. I had phoned the bank after I couldn’t trigger a call even though I had cleared my cookies and history several times using my browser (Firefox) and CCleaner.
Are you finding this use of the IP address as an authenticator somewhat unusual and, perhaps, not so secure?
It’s not a question of finding a cookie safer than an IP address. They are both similarly safe. It’s more a question of stability. A cookie stays on the computer until you delete it, or it expires, and the bank has control of the expiration date of a cookie if it sets one. It’s unpredictable when the IP address changes
Unusual, but I’m good with it.
It’s quite common for 2fa logins systems to leave a cookie after verifying the second factor. The computer with that cookie then serves as a second factor. I’ve never heard of a bank doing that. Generally, they’re more careful because there’s more at stake. That method has a flaw. With your computer being the second factor, someone who has access to your computer, for example, at work can get in if they installed a keylogger, they can access your bank account on that computer. A rare situation but not 0% probability.
My bank does it. “We don’t recognize the computer you’re using”. Then after successfully entering the code, the cookie is optional: “would you like to register this computer?”. I like the approach. I don’t register on portable devices, for example.
I like the idea too. My bank is so picky, I have to get a code from my 2FA app for each transaction even in the same session.
My warning was for people using shared computers. If you use a shared computer for banking or any other sensitive work, clear the browser cookies (CTRL+SHIFT+Delete) when you are finished. Better yet don’t do any sensitive work on a shared computer.
Please Sir I need help, my facebook account was hacked and the password for 2FA was changed for their computer use, when i request for password i won’t get it,Thank you.
The only recourse you have is to carefully follow Facebook’s account recovery process. https://askleo.com/how_do_i_recover_my_facebook_password/
Two factor authentication sounds like a wonderful idea. When it works.
I do not use a smartphone or mobile phone. I have no need for one. I don’t wont one. I have a landline phone. At home.
PayPal try to send me code to my landline but I receive nothing. I have spoken to them at length about this and they say my phone service provider is blocking the call. My service provider say they are not blocking any calls. PayPal say say resolve the issue within a week. After a week nothing changes.
I cannot access my account; I cannot make payment on eBay with PayPal; I cannot sell anything on eBay.
I cannot use many websites that require a mobile phone number as part of the registration.
I am locked out of my savings accounts with the UK government because their system also does not work on a landline.
Wonderful system.
Have I to give up my landline phone and use a mobile phone instead?? Is this the end of home phones??
I don’t know how mobile phone pricing is in the UK, but here, there are services as low as €5 a month. You can probably get a basic (not smart) mobile for under €20 or a similar equivalent in GBP.
If it’s available in your country, you might look at getting a google voice number. It’s free, and can accept texts. (Not sure if it’s available in the UK, though.) https://voice.google.com/
Sometimes I’m too smart for my own good. In my password manager notes section I have a list of 8 items titled “Recovery Codes for Google Authenticator” and the codes are each 10-digit lower-case alphanumeric, no special characters. I have no idea where I got these but the notes entry list was modified in Dec 2019. I’m not asking for a psychic explanation but as mentioned in this article, if my phone was lost or Authenticator was deleted, could these be used to sign in to some account (e.g., Firefox or Facebook) by using one of these codes instead of the code Google Authenticator would have provided OR would one of these codes be used to actually recover Google Authenticator itself? I could not figure out in Google where I could get replacement or additional codes. I don’t know what is meant in this article about “Save those someplace secure. You can log in with each of those passwords exactly once without requiring your second factor.” Log in where, please? Hoping you or your loyal fans have some insights, please? Thanks.